Main navigation
News
by by Henry Wong

With all staff mailboxes migrated to Office 365 (O365), the migration of on-premises email supporting tools is underway. One significant upgrade is the migration of on-premises email anti-spam tool to the O365 Exchange Online Protection (EOP) cloud-hosted email filtering service. The migration has ...
by JUCC ISTF

/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ ? Relationship with ISMS Information Security Management System (ISMS) is defined in the ISO/IEC 27000 set of standards. The ISO/IEC 27001 standard sets out a certifiable and ...
by JUCC ISTF
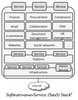
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ ? The NIST Definition of Cloud Computing 1 The cloud model is composed of 5 essential characteristics (Ondemand self-services; Broad network access; Resource pooling; Rapid ...
by ML Lee
In today’s office environment, we often share information like reports, presentations and minutes among colleagues. We have been taught how to connect to the departmental share drive through a network drive letter to store and access files in a traditional file folder structure. This works quite ...
by JUCC ISTF

/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ The term APT was first used by U.S. Air Force back in 2006 to facilitate discussion about a set intrusion activities with specific characteristics. These days, APT is often used ...
by Wilson Wong

Phishing email spreads over the Internet from time to time. You may have received suspicious email telling you that your computer account has problems/will expire/has exceeded quota/etc. and requires you to verify your identity by clicking on a URL (Uniform Resource Locator) to a web page, and then ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ There is a massive upsurge of mobile devices in the consumer market. Corporations are also demanding their employees to have instant connectivity to their working environment ...
by JUCC ISTF

/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ To ensure that data centres meet the reliability and performance needs of universities, and achieve the comprehensive protection from various security threats, a number of aspects ...
by JUCC ISTF

/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Vulnerabilities of data centres are found in their physical security, systems / devices hosted and management procedures implemented. Several common exploitation techniques are ...
by Wilson Wong

What is Information Rights Management? Information Rights Management (IRM) is a technology that protects sensitive information from unauthorized access. It allows information owners/publishers to distribute sensitive information to specific individuals. When an email or a document is protected by ...