Main navigation
News
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Data leakage refers to unauthorised transmission of data from within an organisation to an external destination or recipient. The transmission can be done both electronically and ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Virtual machines are the containers in which guest operating systems and their applications run. In best practise, all virtual machines are isolated from one another. Virtual ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ The virtual networking layer consists of the virtual network devices through which virtual machines and the Service Console interface with the rest of the network. VM Server such ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ All configuration tasks for the VM Server are performed through the Service Console, including configuring storage, controlling aspects of virtual machine behaviour, and setting ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ A virtualisation infrastructure represents an additional architectural layer which can suffer from security vulnerabilities and be the target of attacks. Generally, attacks can be ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ In view of a numerous benefits of virtualisation, virtualisation technology has recently gained popularity in the marketplace. According to Gartner, percentage of workloads ...
by JUCC ISTF
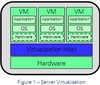
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Virtualisation is the separation of resource or request for a service from the underlying physical delivery of the service. It can dramatically improve the efficiency and ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Code injection attacks pose massive threats to the IT environment within universities. They could allow hackers to compromise universities' network, access and destroy their data ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Code injection attacks typically occur when inputs has not been adequately validated before execution. The basic principle is to provide some form of input with additional ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Websites and web applications are often used by universities for public access and provide required services to their end-users, including staff and students, round-the-clock (e.g ...